In recent years, as the adoption of Web3 smart contracts and decentralized applications (dApps) has rapidly increased, so has the risk of cyber attacks.
Disclaimer: The content of this article is for informational purposes only and should not be considered as financial or investment advice. Users are encouraged to conduct their own research and exercise caution while interacting with Web3 platforms.
The consequences of falling victim to a crypto attackers can be disastrous. For individuals, it means the loss of hard-earned funds and potential damage to their reputation within the Web3 community. Systemically, it undermines trust in the blockchain and has the potential to dampen the overall adoption of decentralized applications.
Given the decentralized nature of Web3, the chances of retrieving stolen funds are often slim, making prevention and proactive measures vital:
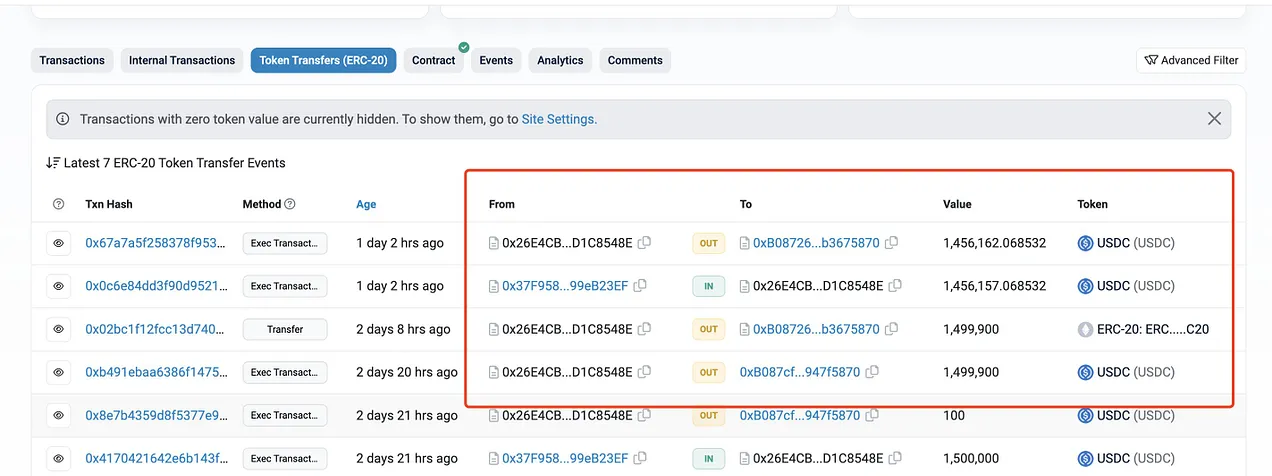
A multi-sign Safe wallet lost $1.45 million to address poisoning attacks! Below/above victim wanted to send it to 0xB087cf…947f5870 but sent to 0xB08726…b3675870!

Typically, the modus operandi of crypto hacker’s kit involves luring users into interacting with malicious DApps or smart contracts. These malicious entities aim to deceive users into depositing their digital assets into a seemingly legitimate transaction, only to ultimately drain those assets into the attacker’s account. Often, attackers leverage a combination of social engineering, fake airdrops, and enticing high-yield investment schemes to attract unsuspecting victims.
These attacks typically target users who interact with vulnerable DApps, often resulting in the loss of their valuable digital assets. One of the most prominent threats to the Web3 ecosystem is crypto drainers attacks, which aim to siphon off funds from vulnerable contracts!
Thankfully, MetaMask has recently launched MetaMask Snaps, a feature aimed at expanding the wallet’s functionality and opening doors for developers and users in the blockchain ecosystem.
To safeguard the integrity and security of Web3 platforms, it is vital for users to utilize robust tools like the W3A Snap developed by web3antivirus (W3A Team) and available as a Metamask snap as well:
So, in this article, we will explore the powerful capabilities of Metamask Snaps and why installing Web3 Antivirus Snap on your wallet is imperative to prevent potential hacks! Let’s get started!
What Are MetaMask Snaps
First things first, MetaMask Flask is a development platform for the MetaMask wallet software. It allows Web3 developers to experiment with new features that will eventually be integrated into MetaMask.
One of these new features is Snaps, a plug-in system that allows users to install plugins that extend MetaMask with custom functionality. A Snap enables traditional websites to access Web3 functionalities, show additional information to users when they send transactions, and perform actions for users at scheduled intervals. For example, whenever a user tries to transfer ERC20 tokens using MetaMask, a fraud detection Snap could check the recipient of the transfer against a list of known scammers.
As another example, a wallet Snap could provide integration with non-Ethereum blockchains, allowing users to perform transactions on these other blockchains from a website that supports the wallet Snap!
W3A Snap TL;DR
With the increasing threat of Crypto Drainers attacks, it is crucial for users to proactively protect their digital assets. This is where the Web3Antivirus Metamask Snap comes into play. The Metamask Snap is an extension that integrates seamlessly with the popular Metamask wallet, providing an extra layer of security against potential threats!
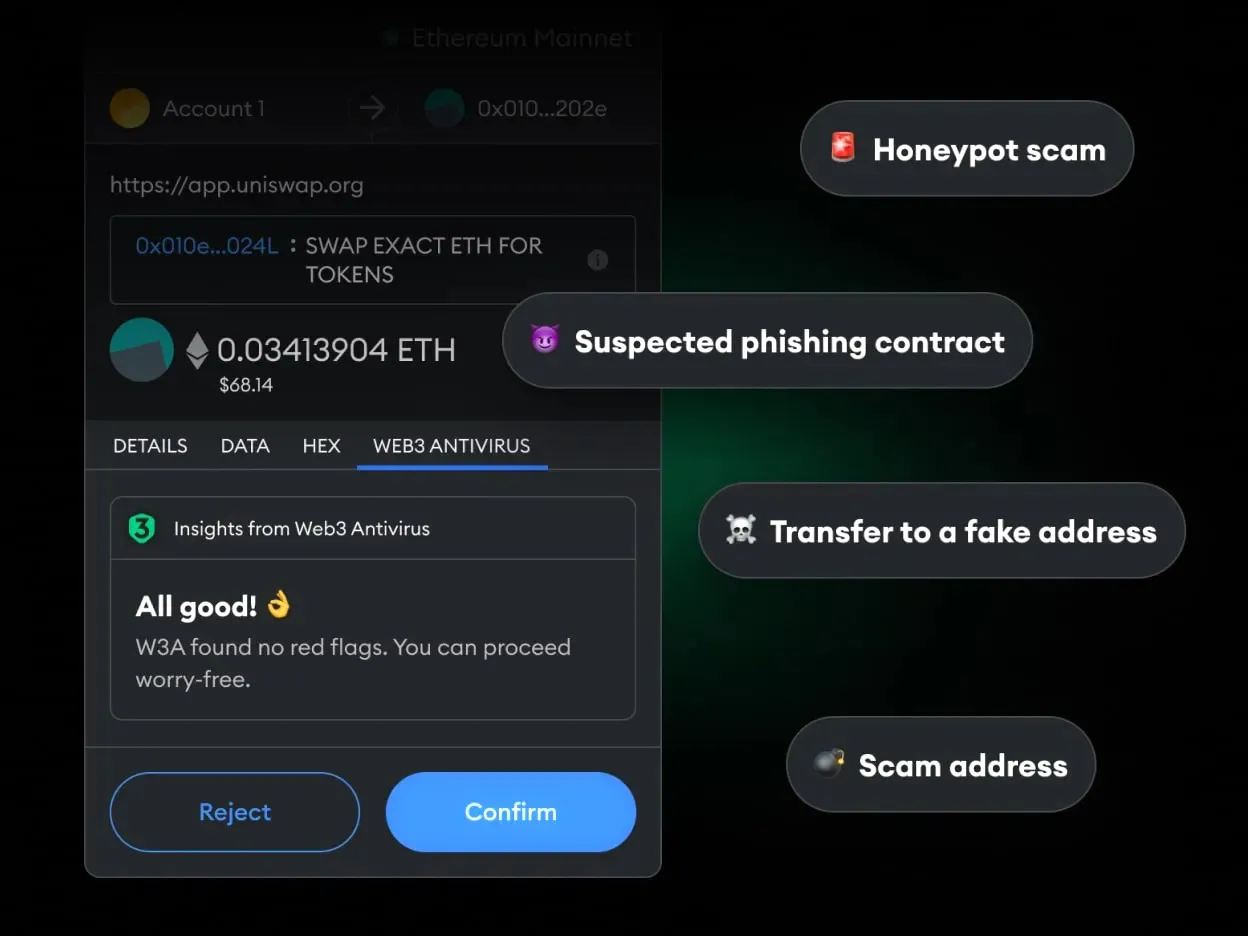
Web3 Antivirus Snap also instantly discovers and warns you about some of the most common Web3 scams: honeypots and poisoning attacks, with additional risk detectors currently in progress. The Snap speaks with you in a simple and straightforward manner, so that you can easily grasp what’s wrong with the transaction.
Currently, the Snap supports only the Ethereum network, but Polygon, Arbitrum, and BNB chain are coming soon!
How Do MetaMask Snaps Work?
Snaps are implemented as JavaScript/TypeScript applications in which developers implement one or more of three functionalities as JavaScript/TypeScript methods (transaction insights, RPC requests, and cron jobs).
Because a Snap can consist of arbitrary code that can access a user’s MetaMask wallet, all Snaps are run in a special environment that is designed with security in mind. Thus, they differ in several ways from ordinary JavaScript or TypeScript code that would be found on, say, a web page or a Node.js application. In particular, the code will be executed in a “sandbox” that limits the JavaScript APIs that can be accessed.
Furthermore, to prevent Snaps from hogging system resources, all Snaps are meant to be “short-lived” in that they do not take too long to generate transaction insights or process RPC requests. Snaps that time out will be terminated by the MetaMask extension.
-
Transaction insights: before a user signs a transaction, a Snap that provides transaction insights will display additional information about the transaction in a popup. This will help make the user make an informed choice about whether to actually sign the transaction.
-
RPC requests: a Snap that processes JSON-RPC requests enables dApps (websites) and Snaps to communicate with the Snap. The user will not actually access this type of functionality directly; rather, the Snap will typically serve as part of the plumbing behind the website/dApp that the user is interacting with.
-
Cron jobs: a Snap that supports cron jobs allows the user to schedule actions that will be automatically performed for the user at regular intervals.
For more details on how Snaps work, I would like to refer the interested reader to the official documentation!
Web3 Antivirus Snap
When it comes to Web3 security, you can never have too much protection. With both the Web3 Antivirus browser extension and the Snap monitoring your transactions, you double your safety measures against Web3 malicious entities!
Web3 users from falling victim to crypto drainers attacks. By utilizing advanced threat detection algorithms, Web3 Antivirus scans smart contracts, identifies vulnerabilities or suspicious patterns, and alerts users to potential risks. This tool achieves this by analyzing the contract’s code, checking for known vulnerabilities, detecting potential security gaps, and ensuring compliance with best coding practices.
Key Features and Benefits of Web3 Antivirus:
-
Real-Time Monitoring: Web3 Antivirus continuously monitors smart contracts, detecting any anomalous behavior or attempts to exploit vulnerabilities.
-
Early Warning Alerts: It promptly alerts users when potential vulnerabilities or suspicious activities are identified, allowing them to take action proactively.
-
Comprehensive Vulnerability Scanning: Web3 Antivirus conducts thorough scanning of smart contracts, identifying potential loopholes, and ensuring adherence to security best practices.
-
Integration with Metamask: The availability of the Web3 Antivirus Metamask snap allows for seamless integration within the popular Ethereum wallet, enhancing user experience and convenience.
-
Community-Driven Security: Web3 Antivirus benefits from a vibrant community of researchers, continuously updating the threat database and contributing to a more secure Web3 environment.
Keep your Web3 protection guard close at hand in your wallet. This Snap thoroughly examines and assesses the safety of all contracts, addresses, and assets that you deal with. It warns you in real time about possible scams if there are risks like poisoning attacks and honeypots!
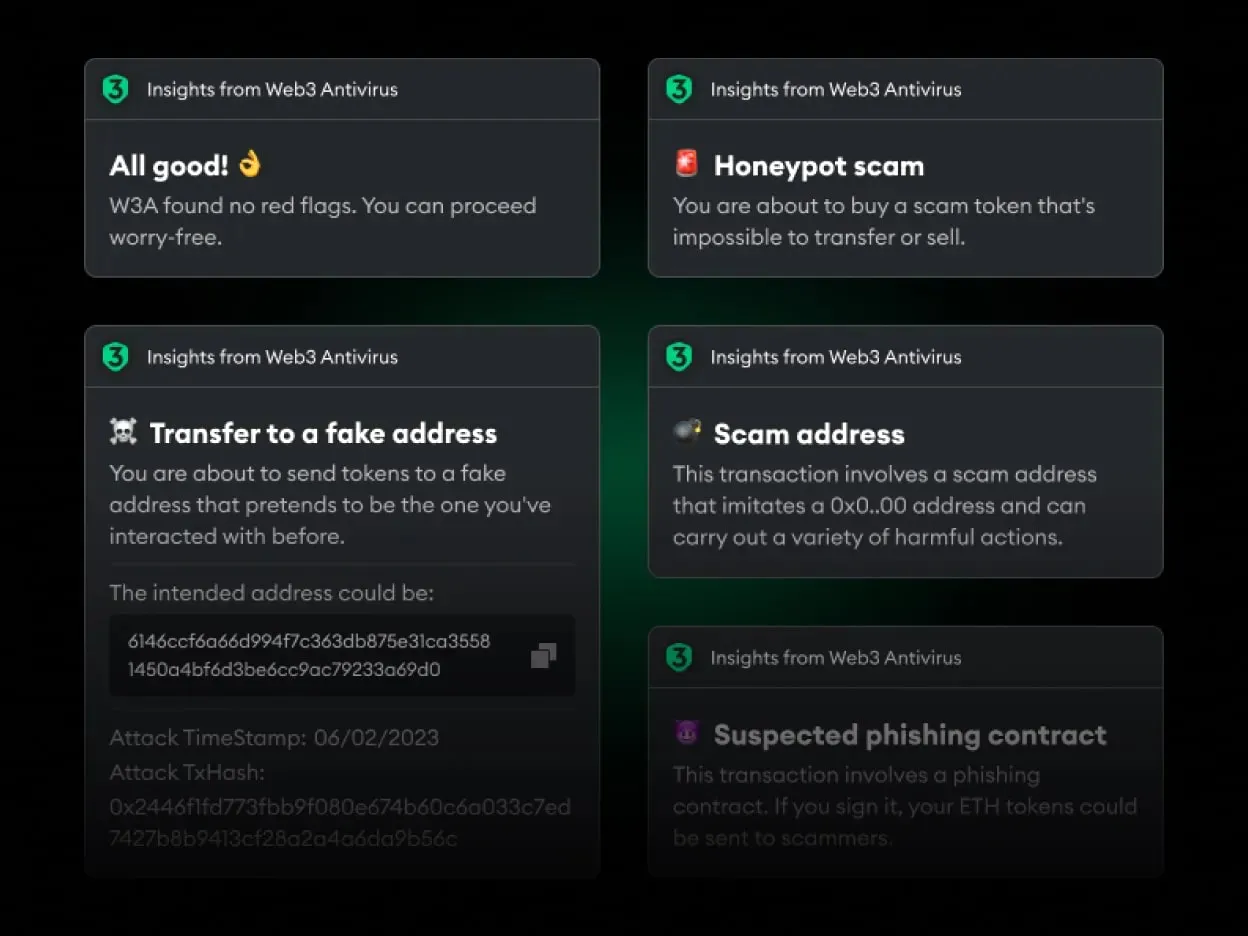
There are several messages Web3 Antivirus Snap can show you. These are:
-
Honeypot scam message signals about a token that you will not be able to resell or transfer after the purchase.
-
Transfer to a fake address message warns you in case the recipient’s address is a scam disguised as an intended address.
-
All good message indicates that the Snap found no risks in the transaction. Currently, the risks detected are honeypot tokens and poisoning attacks.
-
More chains are on the way message is shown when you conduct a transaction on chains other than Ethereum. It is the only blockchain W3A Snap supports at the moment, with Polygon and Arbitrum coming soon.
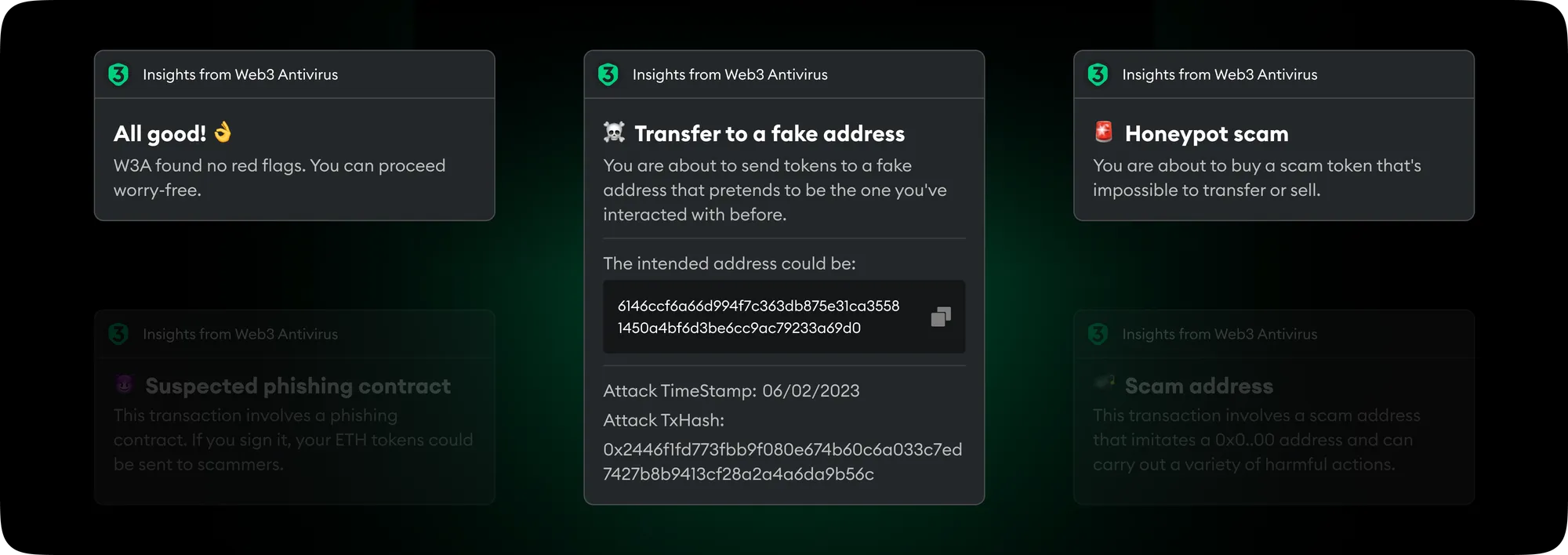
When you initiate a transaction in Metamask, you will see a tab “WEB3 ANTIVIRUS” in a window with transaction details. There, you will find notifications from the Snap.
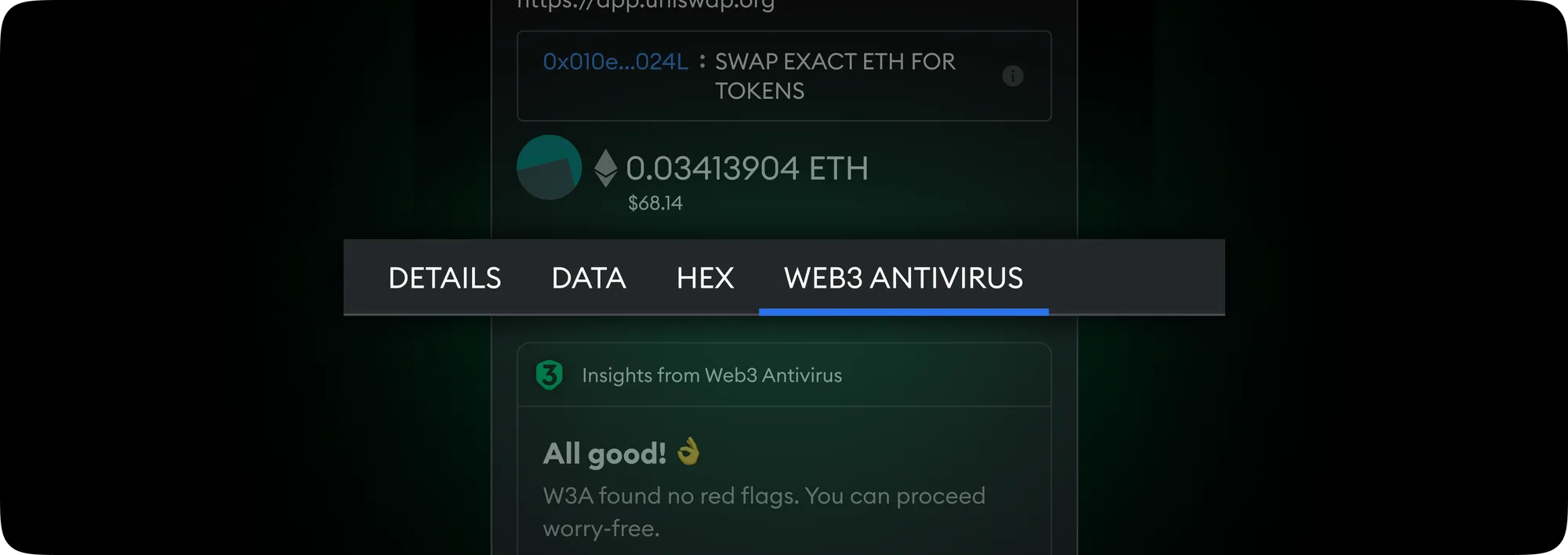
Once you install the Web3 Antivirus Snap, it is always active in your MetaMask and is triggered each time you make a transaction!
Take Back Your Safety in Web3: Web3 Antivirus
The W3A Snap detects honeypots by performing transaction simulations and testing different scenarios: token purchase, transfer, sale, and calculating commissions. If Web3 Antivirus finds that a token can’t be sold, transferred, or it has unusually high commissions, it gets flagged as a honeypot.
But when it comes to Web3 security, you can never have too much protection. With both the Web3 Antivirus browser extension and the Snap monitoring your transactions, you double your safety measures against Web3 malicious entities:
How Do you Detect Poisoning Attacks?
In early 2023, (according to Trezor & CoinMarketCap) a new type of cryptocurrency attack rose to prominence, known simply as “address poisoning.” The premise of the attack is simple: trick the target into sending funds to the attacker’s address by forming transactions designed to confuse the target. Unlike other scams, such as unlimited token approvals or phishing for secret recovery phrases, address spoofing is not as harmful as other methods. However, it can still result in a loss of funds.
The scammers are targeting users of Ethereum and EVMs such as Binance Smart Chain or Polygon. The attack aims to trick victims into transferring their assets to a fraudulent address that is designed to look very similar to their own. The attacker creates a “vanity address” which can be a custom address with a specific set of characters made to look similar to the intended recipient’s address.
When the victim carelessly copies the address from a previous transaction, they may accidentally send their assets to the fraudulent address instead. It’s important to carefully confirm the address before making a transfer to ensure that assets are not accidentally sent to the wrong account.
The attack was first spotted in December 2022 but has since grown dramatically in frequency, with somewhere in the order of $5 to $10 million lost to the scam — a number still growing to this day. At least $2.8 million has been stolen from users on BNB Chain, the majority of which is in the form of USD Coin (USDC) or Tether (USDT). At least 1,000 unique users have now fallen victim to the attack.
-
In the first example, the attacker creates a smart contract that sends tokens with zero amounts to an address that is similar to the victim’s address. The first time the victim sees this transaction, they may not pay much attention to it. However, the next time the victim tries to make a legitimate transfer, they may inadvertently copy the phishing address from the transaction history on Etherscan or their wallet app, instead of the intended recipient address. This mistake results in the victim transferring their cryptocurrency to the attacker’s address.
-
In the second example, the attacker creates a vanity address that is very similar to the victim’s address. They then send very small amounts of cryptocurrency to the victim’s address, hoping that the victim will check the balance on a block explorer and see the attacker’s address in the transaction history. The attacker hopes that when you see a transaction for a token you typically interact with in your transaction history, you might copy the recipient address (thinking it is your own) and then send funds to that address.
Most major blockchains are now being used to carry out the attack. To date, tens of millions of active addresses have been targeted by address poisoning attacks.
The W3A Snap discovers poisoning attacks by scanning all the transactions recorded on the blockchain and looking for suspicious activity characteristic of this type of scam!
Web3 Antivirus Metamask Snaps: Final Remarks
As the adoption of Web3 technologies expands, so too does the need for robust security measures to counter hackers targeting crypto users. Web3 Antivirus provides a crucial line of defense against these threats, helping users protect their assets and ensuring the stability and growth of the Web3 ecosystem.

By utilizing tools like Web3 Antivirus Metamask Snap, users can actively contribute to a safer, more secure Web3 environment and participate in the full potential of decentralized applications. Keep in mind, prevention is key. Stay protected, stay empowered with Web3 Antivirus!
Install the Snap in 3 simple steps:
-
Go to the MetaMask Snaps Directory;
-
Find Web3 Antivirus Snap;
-
Install W3A Snap into MetaMask!
Lastly, remember to always exercise caution when interacting with unknown DApps or smart contracts, and make use of W3A Metamask Snap to ensure a secure and worry-free web3 experience!