In today’s digital age, the safety and security of our cryptocurrencies are of paramount importance. Unfortunately, the risk of hacking and theft is a constant concern. However, there are tools and services available that can help mitigate these risks, ensuring that even if your wallet is compromised, your funds can still be recovered.
I would like to draw attention to the fact that the two services mentioned in the article are unrelated to one another and both offer their services for free. Furthermore, I would like to state that I personally took the entire initiative to write this article!
When your private keys or seed phrase get compromised, bad actors will often put a sweeper bot on your account to take advantage of anything that happens to the address in the future — either you deposit ETH to try and save some tokens, an airdrop happens, or something else.
Every now and then, a hacker might also fail to take advantage of your NFT, stake position, or forget to drain assets from other networks. In these cases, the issue of how to get the remaining money back (un-hacked!) arises urgently.
I won’t go into the details of what MEV and Flash-bots are — you can read the relevant material here!
In this article, we will explore the powerful capabilities of HackedWalletRecovery (developed by Austin Griffith, Speedrun-Ethereum and BuidlGuidl teams) and why installing Web3Antivirus on your wallet is imperative to prevent potential hacks!
Recovering Funds with HackedWalletRecovery
HackedWalletRecovery is a cutting-edge (and absolutely free!) service that specializes in recovering funds from wallets that have fallen into the hands of hackers.
We’ve used it to help a few people that had leaked wallets private keys or seeds and, specifically, sweeper bots. So, if you know anyone who has this issue feel free to send them this article!
When a crypto wallet is compromised, it can feel like all hope is lost… Occasionally, a hacker may overlook stealing your NFT, staking position, or forget to drain assets from other networks. In such instances, the question of how to recover the rest of (untouched by hacker!) money emerges.
The outcome can be the same regardless of how you were hacked — whether you lost your private keys, made a poisoned signature or approve, or whatever else.
HackedWalletRecovery successfully recovers funds that would otherwise be lost forever. It is important to note that time is of the essence.
The longer a compromised wallet remains in the hands of a hacker, the more difficult it becomes to recover the funds. However, this is what you should do first:
-
Revoke approvals via revoke.cash or cointool.app or app.unrekt.net or these tools or web3antivirus.
-
Blind signing is also dangerous! Use transaction simulators & multi-sig.
-
Establish endpoint cluster (use On-Chain Investigations Tools List ) and contact them.
-
Report your case here: chainabuse.com & cryptoscamdb.org or phishtank.org
Once again, do not hesitate to contact/tag/email CEX’s support, wallet’s support, stable-coins operators, and relevant protocols! Email or message costs 0$ for you, please keep this in mind!
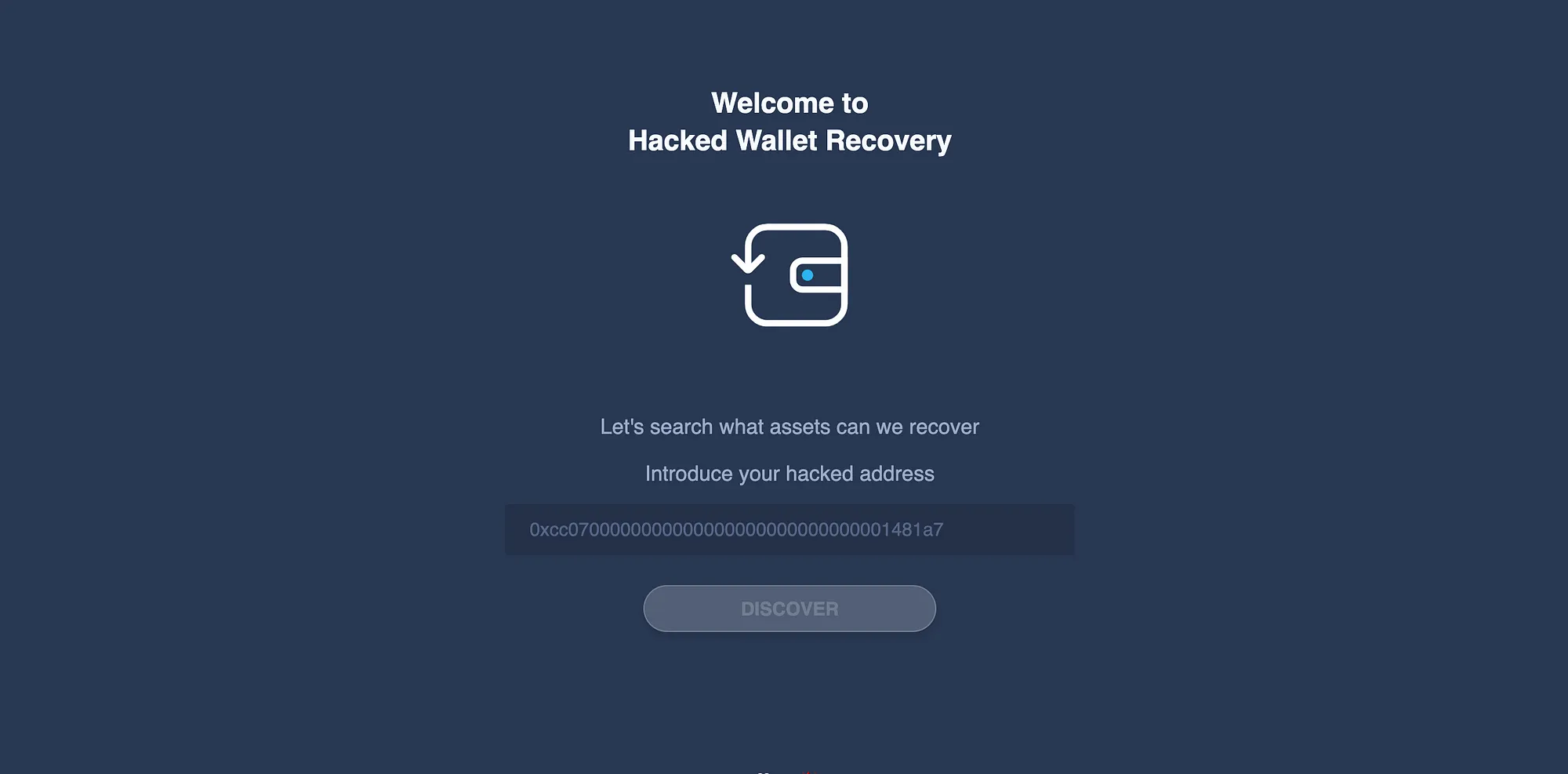
After completing the checklist presented above, seeking professional assistance from services like HackedWalletRecovery as soon as you suspect your wallet has been compromised significantly increases the chances of successful recovery! Follow these tips below:
-
Choose Your Assets. Choose the assets you wish to transfer from the list, or manually add any missing ones.
-
Review the Transactions. Take a moment to review the transactions being generated for asset recovery.
-
Recover Your Assets. Follow the steps to retrieve your assets, this is a critical process so please be patient.
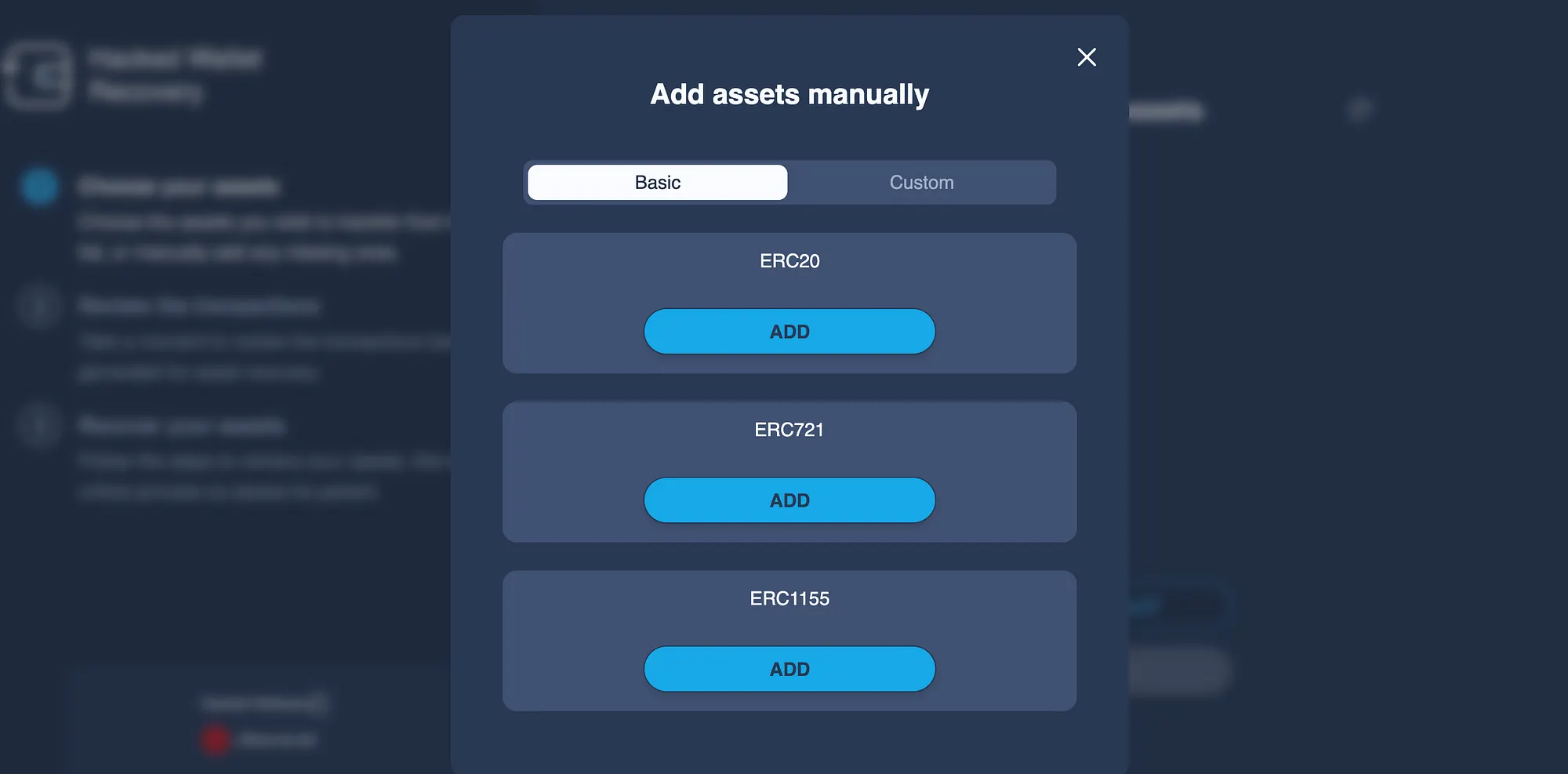
Everything ought to happen naturally, but if you run into any issues, don’t hesitate to get in touch with the article’s author (me!) for assistance!
HackedWalletRecovery: In-Depth
To understand better how HWR works let’s take a look at an older version of it — in many ways, it’s based on its mechanics!
Simply speaking, searchers use Flashbots to submit bundles to block builders for inclusion in blocks. Bundles are one or more transactions that are grouped together and executed in the order they are provided. In addition to the searcher’s transaction(s) a bundle can also potentially contain other users’ pending transactions from the mempool, and bundles can target specific blocks for inclusion as well.
So, back in 2022, one amazing researcher made this simple flashbots bundler app to help people with white-hat recoveries of compromised accounts. You can easily use this app to send needed ETH to your compromised wallet, transfer funds and NFT out without being front-run by the sweeper bot:
You can use the UI to generate a new flashbots rpc, build the bundle by sending ETH for gas, then the recovery TX, then withdraw remaining funds. Then when you hit submit bundle it goes through a relayer which is maintained by the community! Here’s a video walkthrough:
If you use it, I recommend paying around 3x the gas price to get included. And make sure your bundle is over 42k gas or it will be ignored by the network. Also, check out this awesome recovery solution for ERC721!
Additional Resources & Tips
PSA to anyone who checks their accounts daily to make sure they didnt get hacked — set up a Watch List on Etherscan to notify you of any transactions from your addresses. It’s free and the notifications come quickly. Could buy you some valuable time while the hacker is still doing test transactions: etherscan.io/myaddress or use aml-bot!
MEV & Recovery Tips
-
If you need additional assistance, feel free to reach out to whitehat.flashbots.net — a group of white-hats organized by Flashbots that help users recover funds leftover from hackers.
-
If you have an urgent (and/or potentially massive) situation and need help or a contact, please message us via seal_911_bot. You can also reach out to Mycrypto or Defiac!
-
Check out this super simple contract allowing a target wallet to attempt to recover a token quickly in the event it is comprised or locked out / keys lost.
-
To ensure there’s no ETH in the compromised account, it is highly recommended running a burner bot!
Bitcoin Recovery Solutions
-
For Bitcoin there was a similar solution — you can use something like this or this.
-
Check out Accelerator (Choose Paid accelerating) and Broadcatst!
-
Save & share this note if you know someone who has been scammed or hacked or/and lost crypto!
The Role of Web3Antivirus in Preventing Hacks
This post is also a logical continuation of my previous one, which you should read immediately if you haven’t already in order to gain a better understanding of OpSec (Operational Security) and Threat Modeling before proceeding to the current one:
While the recovery of funds lost to a hacker is crucial, it is equally important to proactively protect your wallet to avoid such scenarios altogether. Simply speaking, Web3Antivirus functions by scanning wallet interfaces and detecting suspicious or malicious activities in real-time.
It alerts the user when it detects potential threats, such as phishing attempts, malware, or unauthorized access attempts.
By installing and utilizing Web3Antivirus, you can significantly reduce the risk of falling victim to hacking attacks. Investing in such measures not only provides peace of mind but also helps to maintain the security of your hard-earned funds!
Final Remarks
In a world where hackers constantly seek to exploit vulnerabilities, it is crucial to prioritize the security of our crypto wallets.
By having a reliable recovery option like HackedWalletRecovery and complementing it with the proactive protection offered by Web3Antivirus, users can confidently navigate the cryptocurrency landscape, knowing that their funds are safeguarded.
Keep in mind, prevention is better than cure. Take the necessary steps to secure your wallet and always stay vigilant. With the right tools and precautions in place, you can protect yourself from potential hacks and ensure the longevity and security of your digital assets.