We will gradually expand the capabilities of our Pessimistic Spotter on-chain monitoring & defense service and provide additional details in the subsequent digest piece!
Follow:
-
spotter.pessimistic.io — Sign-up!
-
pessimistic_spotter_public — Spotter Public Alerts Channel (Telegram)
-
blog.pessimistic.io — Follow our blog!
Ndxfi DEGEN token Exploit: Thoughts
As you are probably aware, on March 20th, a series of transactions involving the Ndxfi DEGEN token resulted in an attacker profit of approximately 110 ETH! The initial root cause was the incorrect calculation of the tokenAmountOut value by “calcSingleOutGivenPoolIn()”…

The original attacker submitted to mempool with low gas and was frontrunned by an MEV bot:
-
Original attacker: 0x7ab8c3807f97eb2bdc52d4947690d726a33062a1
-
Deploy TX: 0x9bd43de5049d44785703d20b85c349c70be7ae84f9569d864938ca31315843e1
-
MEV bot that seems to have picked up most of the profit: 0xd050e0a4838d74769228b49dff97241b4ef3805d
There is also a take that it was rather a balancing arbitrage which takes advantage of the fact that weights haven’t been updated for DEGEN for a year than an actual attack. Anyway, this does not change the fact that, among other things, we could protect the project from this as well.
Our Spotter system detected this attack before it actually happened!
The system successfully operated and took action very quickly (it recognized an attack and thus performed the first step — detection), demonstrating once more that it is possible to then pause contracts, launch counterattacks, and take other actions when connecting the experimental part of the Spotter to the supported project…
To put it another way, our system operates in an experimental mode, and the test indicated that we would have sufficient time to respond:
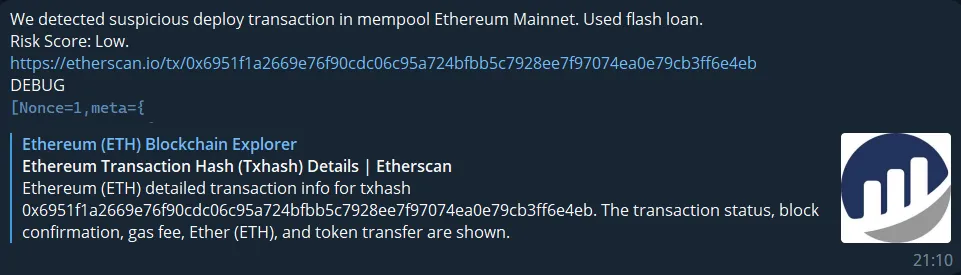
There were at least three different approaches that we actually could take in order to counteract this attack, presuming that it would occur to the supported protocol in the same manner that it occurred to Ndxfi (on a public pool):
-
Сounter-attack hacker via MEV bots (since this exact attack was performed on a public pool) land then return the money to the project.
-
Put the contract on hold (pause) through the integration with the project (keep in mind — in this exact case, Ndxfi was not our customer/supported project). Check out this article to know more about operational changes in live contracts.
-
And finally, to slow down the attack through the connection with the validators and offer the hacker a bounty beforehand (read more about it here).
It is important to mention that currently our system does not counter-attack (and does monitoring only) as we first need to sign a contract with the protocol. Nevertheless, we have confirmed the theoretical possibility of active protection and will continue our research in this direction:
Pessimistic.io News
Some news from our ‘‘parent’’ auditing company that we think is important enough to mention!
- In particular, article about Сhainlink VRF has been published and endorsed as we continue our research:
- We are happy to report that Spotter is becoming more and more popular and is getting the attention it deserves:
-
This week we came across an interesting protection implementation from a third-party team (not connected with us), and we promise you to explore it separately this month and explore the possibility of applying similar solutions to Spotter. Read our oldie but goodie research about Reentrancy Attack — one of the attacks that used to be very common in the Web3 smart contract-based projects, but has recently been relegated to the background, although they still pose a great danger! Check out this repo as well.
-
We are currently doing some research — including exploring new tools and their possible use in our Spotter project, of which we want to highlight the Forta V3. We will continue our research work in this direction in the future!
To make sure you don’t miss anything, subscribe to our blog! All articles are also posted on my (Officer's Notes) personal Mirror blog:
Follow:
-
spotter.pessimistic.io — Sign-up!
-
pessimistic_spotter_public — Spotter Public Alerts Channel (Telegram)
-
blog.pessimistic.io — Follow our blog!
-
twitter.com/sadspotter — Follow us on Twitter!
We also hope for your support because we think this market is crucial, first and foremost for the overall security of our industry!
You can subscribe to our blog to make sure you don’t miss any of the regular news and updates we plan to publish on the project in a special digest!
In the following articles we will gradually expand the functionality of our service and provide an opportunity to test it on your system. We’ll let you know the release date soon, stay tuned! 🙂
Thank you very much for your attention!
Support is very important to me, with it I can do what I love — educating users!
If you want to support my work, you can send me a donation to the address:
-
0xB25C5E8fA1E53eEb9bE3421C59F6A66B786ED77A or officercia.eth — ETH, BSC, Polygon, Optimism, Zk, Fantom, etc
-
4AhpUrDtfVSWZMJcRMJkZoPwDSdVG6puYBE3ajQABQo6T533cVvx5vJRc5fX7sktJe67mXu1CcDmr7orn1CrGrqsT3ptfds — Monero XMR