Greetings, dear readers! We continue our series of educational articles and today we’ll study how to secure your NFT project!
In this article, I’ll give audit and development tips, as well as put together well-known resources in the SoK!
Make sure to read the rest of the series:
I will also share our own observations and give some advice in the next article in our series, since our team has been working since 2016, we have accumulated quite a few of them.
First and foremost, I would like to express our sincere gratitude to the authors of all the resource materials, and of course our pessimistic.io auditors who have helped me so much by revealing needed information and lifting the curtain of secrecy!
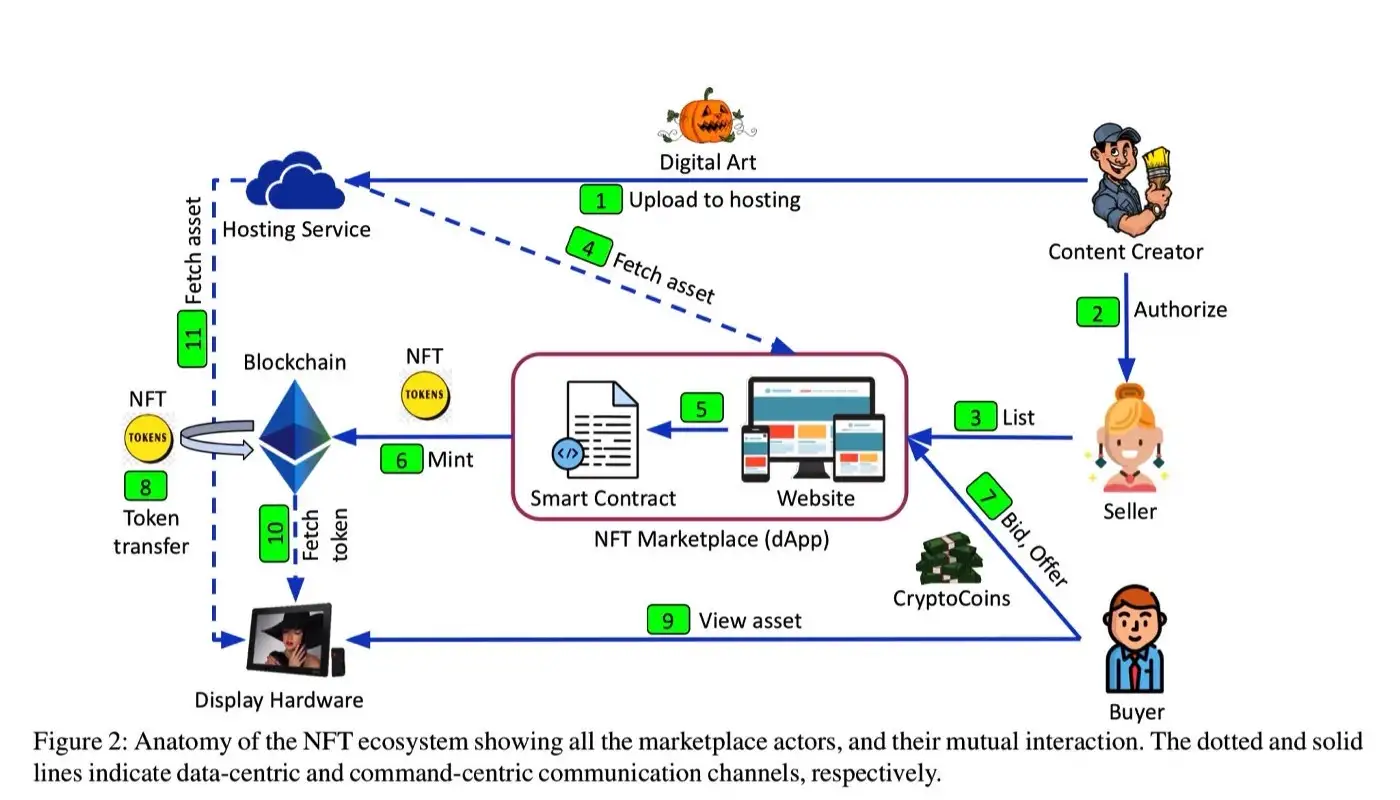
There have been several instances of NFT hacking and exploitation in the past, and it’s important for NFT users to be aware of these risks and take steps to protect their assets!
We believe there is no one who doubts that the basis of any secure integration is a special approach to writing code. Consequently, this article will be focused only on those aspects that can be really useful for making your code safe and secure!
Therefore, below you will see not a typical article, but a Systematization of Knowledge — SoK, in which I will rely on Authors that I myself trust in this matter, and of course our pessimistic.io auditors! Let’s get started!
By the way, here are some vacant slots in the first quarter of 2023 now so if your project needs an audit — feel free to write to us, visit our public reports page here! Let’s get in touch: gm@pessimistic.io!
I — We Recommend
Since our team has been working since 2016, we have accumulated quite a few observations, which we will share below along with several security advices:
-
If the contract has .(safe)transferFrom, then in 99% of cases from parameter must be msg.sender. Otherwise hacker can take advantage of other user’s appovals and rob them!
-
If there is .transferFrom in the contract, users must not manage the from parameter. Otherwise hacker can take advantage of other user’s appovals and rob them! In 99% of cases from should be just msg.sender.
-
Remember that the OpenZeppelin implementation of ERC721 and ERC1155 vulnerable to reentrancy attacks, since safeTransferFrom functions perform an external call to the user address (onReceived)!
-
On-chain “random” (based on gas cost, block hash, and stuff like that) is unreliable, it can be bypassed (e.g., one can buy specific NFT). Consider using Сhainlink VRF or a custom solution based on something like random.org!
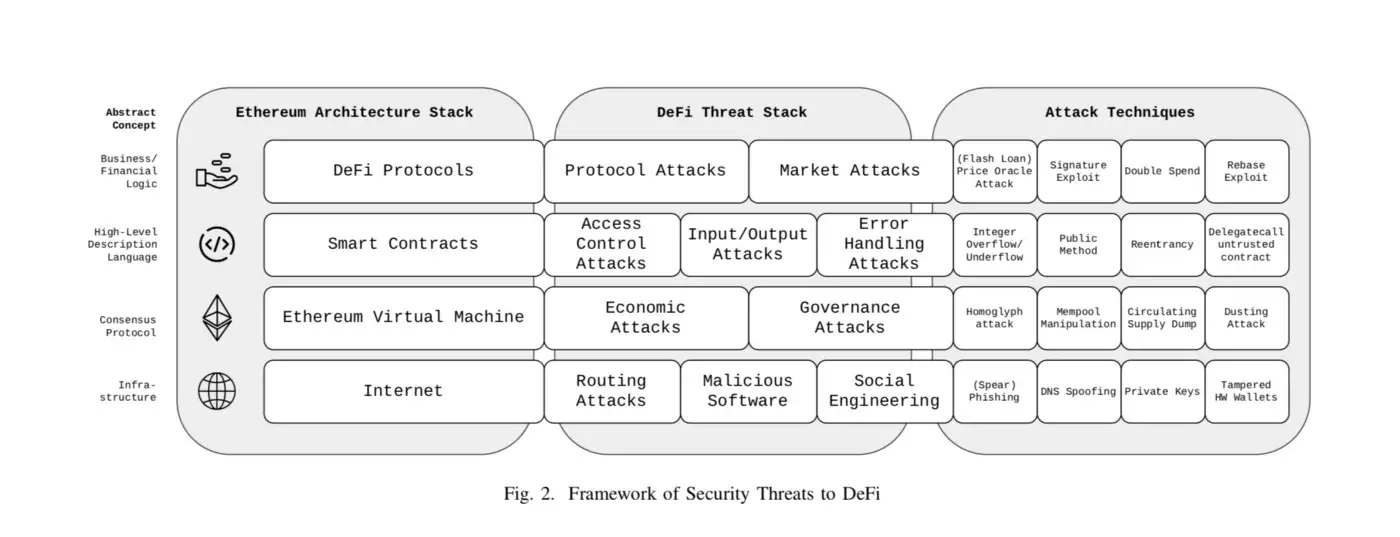
II — A Tiny Tip
Keep in mind that NFTs which are being added to the marketplace by users can be malicious themselves!
TLDR: The trick the platform in turn allows assets to be uploaded as files up to 40 MB in size with any of the following extensions: JPG, PNG, GIF, SVG, MP4, WEBM, MP3, WAV, OGG, GLB, GLTF.
Knowing this, experts on video uploaded an SVG image containing malicious JavaScript code to OpenSea. When they clicked on it to open it in a new tab, they found that the file was running in a subdomain of storage.opensea.io. The researchers then added an iFrame to the image to load HTML code that would inject the window.ethereum request needed to establish a connection to the victim’s Ethereum wallet.
Use scanning (1, 2, 3) or other methods of protection. Be aware of possible Passive XSS or Iframe attacks!
It is very important to mention that Sandboxing also prevents the iframe from importing its own MetaMask (or, let’s say, frame.sh) instance!
III — Data Sources
NFT attack vectors:
-
Profanity: Clarifications (suggest using this safe tool instead)!
-
What’s in Your Wallet? Privacy and Security Issues in Web 3.0.
Check out:
Researches:
-
All Known Smart Contract-side and User-side Attacks and Vulnerabilities in Web3
-
Attacking the DeFi Ecosystem with Flash Loans for Fun and Profit
-
NFT Wash Trading: Quantifying suspicious behaviour in NFT markets
Front-end security:
OpSec:
Pre-Audit:
Yet another tiny (non-binding) tasks you should do before an audit:
-
Before an audit, make up your Tech docs - be sure you have an architectural diagram, NatSpecs & Code comments;
-
Provide extensive unit/integration testing suite;
-
You should have a list of protocol invariants somewhere…
Thank you!
We hope that this article was informative and useful for you! Thank you for reading!
What instruments should we review? What would you be interested in reading about?
Support is very important to me, with it I can do what I love — educating users!
If you want to support my work, you can send me a donation to the address:
-
0xB25C5E8fA1E53eEb9bE3421C59F6A66B786ED77A or officercia.eth — ETH, BSC, Polygon, Optimism, Zk, Fantom, etc
-
4AhpUrDtfVSWZMJcRMJkZoPwDSdVG6puYBE3ajQABQo6T533cVvx5vJRc5fX7sktJe67mXu1CcDmr7orn1CrGrqsT3ptfds — Monero XMR