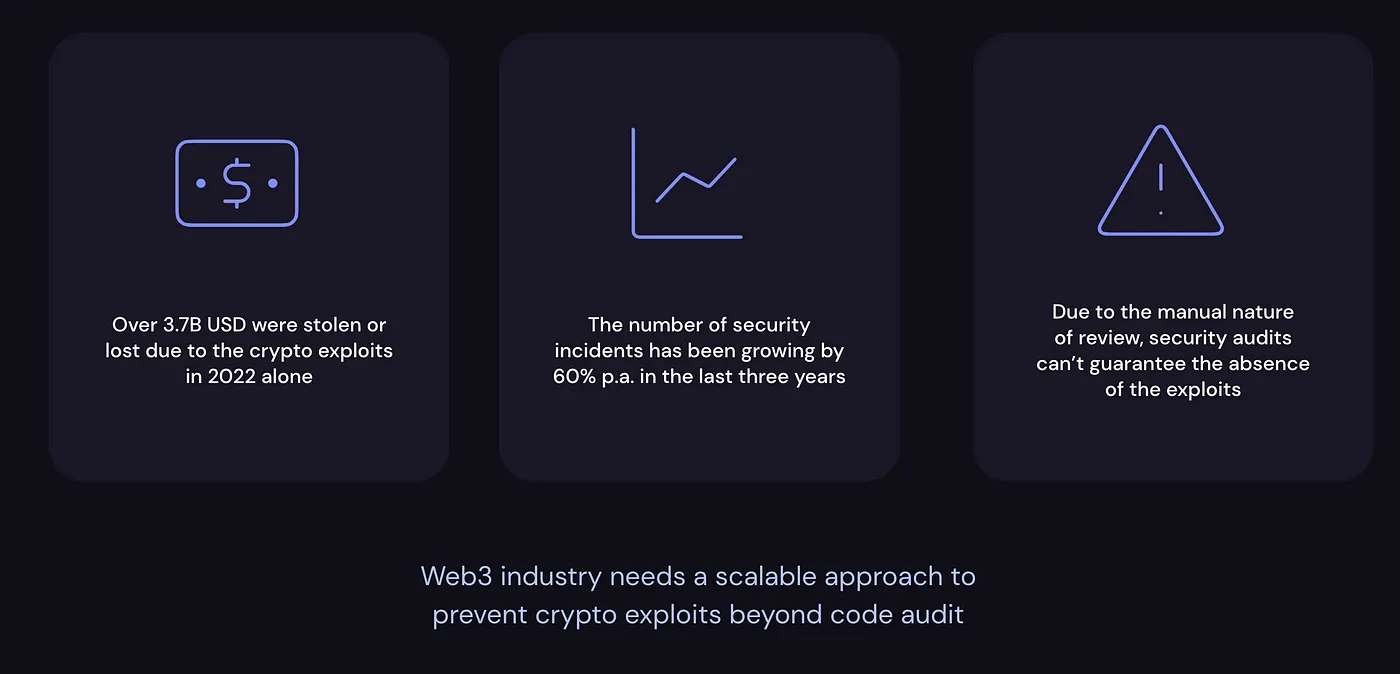
Looking at this month’s never-ending hacks, one may wonder why they happen so frequently…
Have audit firms actually gotten worse at what they do?
This, in our opinion, is not the case; yet, the topic is rather tricky because, in certain ways, you can reduce the risks to yourself and your project. Yet how? Let’s examine this carefully!
Check out our Pessimistic’s Spotter On-Chain Monitoring & Active Protection Service: t.me/attackdetectorbot
That said, hacks began to threaten our entire market, and as experience has shown, in order to protect yourself reliably, you must be one step ahead of the hacker, so we devised the concept of monitoring and active defense for both blockchain-based projects and their users!
So today, in the following digest piece, we’ll talk about the most recent news, how it affects (and will affect) industry and our Spotter project, and, of course, we’ll explain our Pessimistic Spotter on-chain monitoring & defense service functionality in a more detailed way. Please read our previous article so you can get a better understanding of Spotter’s background and the development process:
According to the questions, the audience has several points that need to be discussed further. That’s exactly what we’ll do next! Let’s get it started!
Pessimistic Spotter: Overview
Check out our Pessimistic’s Spotter On-Chain Monitoring & Active Protection Service:
Risk mitigation is not something to set and forget; it’s a continuous process of monitoring, updating, and refining processes based on evolving market conditions. So, we updated the Spotter Telegram Bot to the public version.
But first, I’d really like to ask you to read our previous articles from which you can learn about the history of Spotter and the progress of development:
Spotter: In the Wild
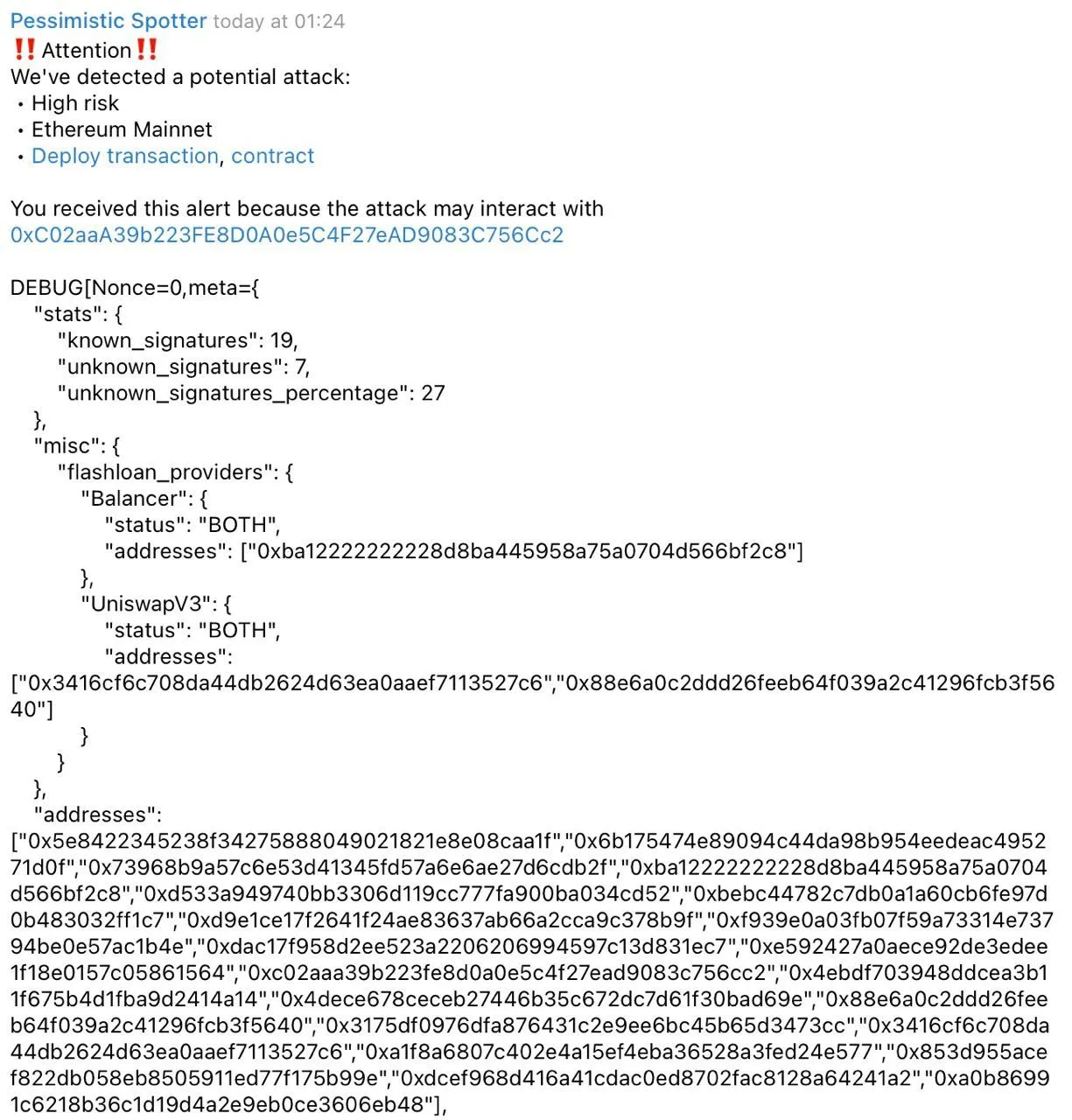
We also glad to state that our system spotted an attack (2M$ loss) on Zunami Protocol before it was even executed! Another win of our system, once again confirmed — the Spotter project could have prevented the attack!
The system successfully operated and took action very quickly (it recognized an attack and thus performed the first step — detection), demonstrating once more that it is possible to then pause contracts, launch counterattacks, and take other actions when connecting the experimental part of the Spotter to the supported project.
In other words, our system is in an experimental mode, and the test indicated that we would have enough time to respond:
We made the onboarding and the customization as easy as possible, so now you are able to set up alerts in 5 minutes. Our proactive alert system against crypto exploits has only gotten better over this time!
Try it for free ⬇️
Please subscribe to our blog to make sure you don’t miss any of the regular news and updates we plan to publish on the project in a special digest:
Configuring Spotter’s API
You can configure the alerts using a Telegram bot, and then use the /genkey command to get the API key. Based on the signals from API, you can then set up any defense action:
Using JSON-RPC Requests to Access WebSockets
-
The
tg_listenJSON-RPC method allows you to receive Spotter alerts; -
To begin, use
/genkeycommand in Spotter telegram bot.
Authenticate
Authentication for this API must be performed via using an API key token. The API key token should be included in the endpoint URL using the key parameter:
wss://api.spotter.pessimistic.io/v1?key=API_KEY_TOKEN
Replace API_KEY_TOKEN with the actual API key token. You can generate new API key in telegram bot via /genkey command.
Subscribe to New Alerts
Next, get ready to send WebSocket requests to the API. You can use command line tools like wscat or make requests from your project. When using wscat, you can send requests as follows:
- Create a Subscription Request:
{
"jsonrpc": "2.0",
"method": "tg_listen",
"params": [],
"id": 1
}
- Response Example:
{
"result": "0x44110d93799b5ab5",
"id": 1
}
- Example of an Incoming Alert:
{
"tx_hash": "0x35ad6c6f783c5327a52319f1cc8fc8eef0218d83adfa6bdbdda5367c1e0a6705",
"risk_score": "high",
"subscribe": {
"chainId": "0x1",
"address": "0xC02aaA39b223FE8D0A0e5C4F27eAD9083C756Cc2",
"calls": ["0x06fdde03"],
"funcs": [
"0x095ea7b3",
"0xd0e30db0"
]
}
}
-
"risk_score"-"med"or"high" -
"address" -
"signatures" -
"calls" -
"funcs"
Getting Started with Defender
This configuration demonstrates the process of implementing contract pausing afterwards to getting an alert from Spotter:
-
Create a Defender relay and send some native currency (ETH, BNB, etc) to this address, so it can cover transaction cost;
-
Create a Defender autotask with webhook trigger and connect your relayer to it.
The autotask code that will be used to pause your contract is demonstrated here:
const { Relayer } = require('defender-relay-client');
const { ethers } = require('ethers');
const your_contract = "0x72876a20Ca6b383b5401CD5FC97ed693d26dF43C"
exports.handler = async function(event) {
if('subscribe' in event.request.body
&& 'address' in event.request.body.subscribe
&& event.request.body.subscribe.address == your_contract) {
console.log(event.request.body.subscribe);
const relayer = new Relayer(event);
let ABI = [
"function pause()"
];
let iface = new ethers.utils.Interface(ABI);
const tx_pause = await relayer.sendTransaction({
to: your_contract,
value: 0,
gasLimit: '100000',
speed: 'fast',
data: iface.encodeFunctionData("pause", [])
});
console.log("tx pause sended", tx_pause.hash);
}
return "ok";
}
Using /Webhook
- Use
/webhookcommand in Spotter telegram bot and send URL webhook from Defender!
Spotter Setup
In Spotter, use the /addcommand to sign up for alerts for the relevant addresses. For the example above this was 0x72876a20Ca6b383b5401CD5FC97ed693d26dF43C on BSC.
In conclusion, we would like to say that we hope that this article was informative and useful for you! Thank you for reading!
We at pessimistic sincerely hope you find our work useful and appreciate any feedback, so please do not hesitate to contact us! The best answers and questions may be included in the next blog post. We hope that this article was informative and useful for you!
Stay safe!
Support is very important to me, with it I can do what I love — educating users!
If you want to support my work, please consider donating me to the address:
-
0xB25C5E8fA1E53eEb9bE3421C59F6A66B786ED77A or officercia.eth — ETH, BSC, Polygon, Optimism, Zk, Fantom, etc
-
4AhpUrDtfVSWZMJcRMJkZoPwDSdVG6puYBE3ajQABQo6T533cVvx5vJRc5fX7sktJe67mXu1CcDmr7orn1CrGrqsT3ptfds — Monero XMR