In the rapidly evolving world of Web3 technology and decentralized applications, the security of smart contracts plays a critical role. As the adoption and usage of Web3 platforms continue to grow, so does the potential for vulnerabilities and exploits.
To mitigate these risks, developers and projects turn to two crucial practices: bug bounties and audits. In this article, we will explore the importance of bug bounty programs and smart contract audits, highlighting their essential role in ensuring the integrity and security of Web3 systems!
Stay up to date on coming announcements, join the server below:
There is no doubt that the problem of security has recently become very urgent due to the enormous number of hacks and security incidents in the Web3 sphere. Everyone has very different ideas and suggestions on this topic, so we will only attempt to describe a portion of them today. In other words, let me tell you a little bit about what I think is going on in the mind of a typical Web3 entrepreneur and how they feel about bug bounty in general!
So, what are the chances of enhancing current techniques with additional security, and how precisely is the security of the protocol formed in terms of audit and logic?
This time, I will be drawing on the work of other authors, which, of course, I will let you know. In my previous article, I tried to highlight a few basic flaws, but I still missed some crucial ones:
I hope you will enjoy our highly stoichiometric discussion because I’ll also be letting you know about a promising project Remedy!
Revealing True Industry Potential Through the Ultimate Web3 Security Ecosystem
Bug bounty programs are well-established frameworks that incentivize the discovery of vulnerabilities within a system. They offer rewards, typically in the form of cryptocurrency, to individuals or groups who successfully identify and report bugs. In the context of smart contracts, bug bounty programs have emerged as an effective approach to crowdsource security testing, ensuring a broad network of experts working diligently to identify potential vulnerabilities before they are exploited maliciously.
Traditional security models rely solely on internal (or external auditing) teams to identify vulnerabilities, which limits the scope and perspective of assessment. In contrast, bug bounty programs tap into the collective intelligence and diverse skill set of a wider community. By opening this cooperative model to security researchers around the world, developers gain access to a highly motivated pool of talent, boosting the chances of spotting even the most hidden vulnerabilities.
Smart contracts operate in ever-changing and dynamic environments, making it challenging to anticipate every possible scenario independently. Bug bounty programs encourage real users and security researchers to interact with the deployed contracts, pushing the boundaries and testing them in various contexts. This real-world testing helps identify vulnerabilities that may go unnoticed during formal audits, thereby strengthening the overall security posture of Web3 smart contracts.
So…on the one hand, Bug Bounty serves directly as an endpoint for the hacker!
I call this the “classic” bug bounty attitude. That is, the business is interested in giving the hacker a choice in case he has the opportunity to hack the company in some way. Now let’s talk about a newer scheme. In that case, Bug Bounty serves simply as a service. Like another support line or another mail for communication.
In the new formation, however, things are different. In my opinion, what is happening to the sphere now is another logical strike, but on a different level. This is essentially what the English idiom “fight fire with fire” means. It’s its own community of counter-hackers interested in the findings.
Cool Scheme On Topic:

Hacks like the one that occurred lately typically happen as a result of organizations running too many upgrades… There are too many!
Contracts should always be redeployed, fixed, and updated… Auditor work is much slower and takes more time. Companies in this situation are pursuing the number of people and introducing upgrades faster than they have time to check, and it’s unexpectedly not their fault — after all, they do business and are quite confident in what they do.
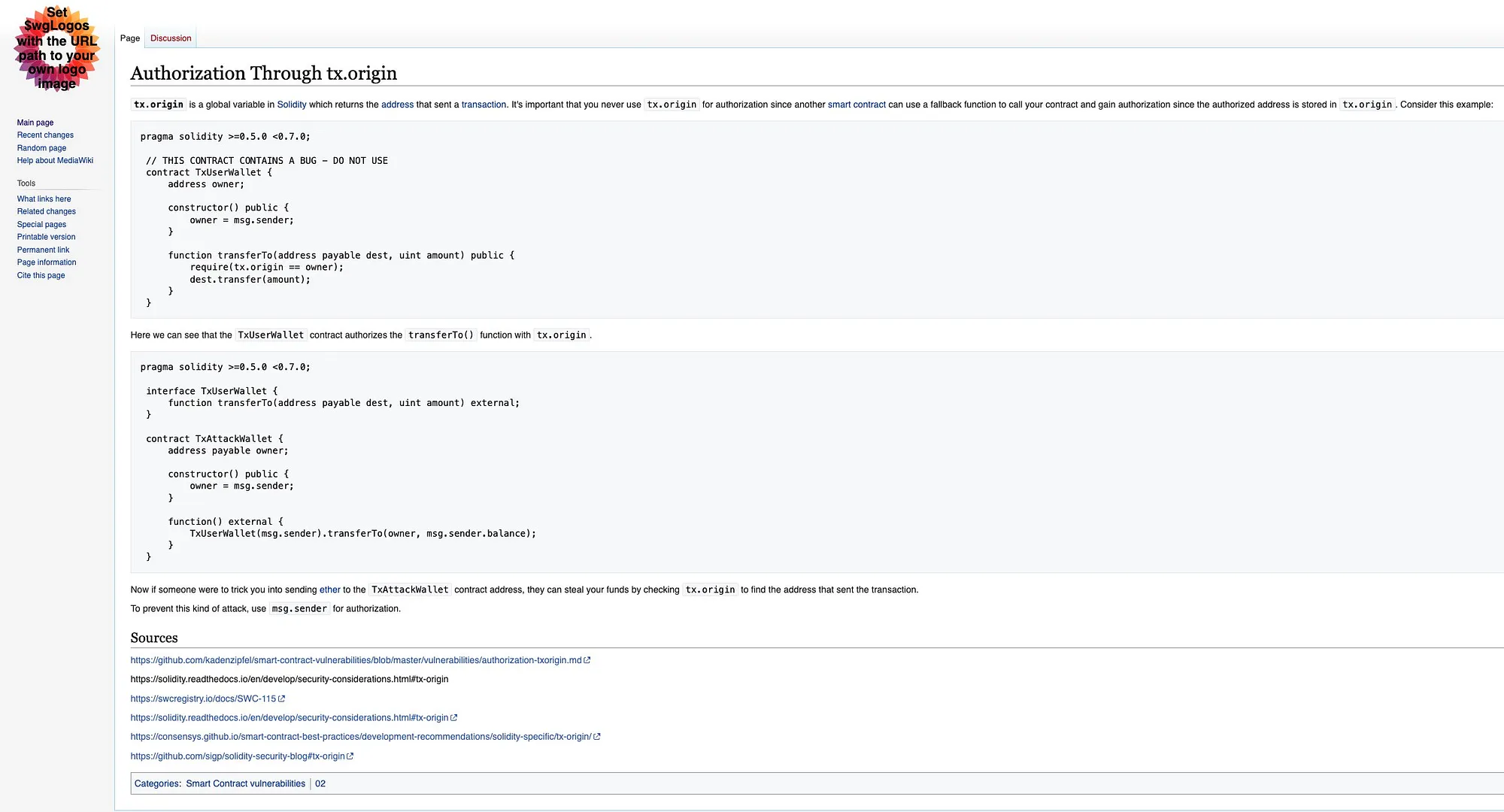
A comprehensive collection of Web3 security vulnerabilities in smart contracts, blockchains, and zero knowledge.
At the same time, many projects discover about the occurrence after it has occurred, when there is almost nothing they can do and can only try to comfort their own community, which will have no effect unless serious action is taken to protect the project. Often companies find out about new incidents right from Twitter/X, you might not believe it, but it’s true!
However, few people know that there are solutions that make it possible to do the proper level of protection on blockchain as well.
As Web3 technology continues to gather momentum, it is imperative to prioritize the security of smart contracts powering these decentralized applications. Bug bounty programs and smart contract audits are integral to the ecosystem, enhancing security, reducing vulnerabilities, and improving overall confidence in Web3 platforms.
By collaborating with the global community of cybersecurity researchers and conducting comprehensive audits, projects can fortify their smart contracts, driving the secure adoption of Web3 applications for a better decentralized future. All this leads us to the idea that in the end it will be important for the project to have multiple levels of protection — several audits from different companies and several bug-bounty programs on platforms with different features.
It’s All About Experience
I think it’s important to think about mind protection as well… It’s like military special forces training — it’s all about experience. If a person hasn’t had that experience (e.g., never been in a situation where mud, water caused by explosions hit your face), they probably won’t be able to deal with the threat.
That’s why in training they have firecrackers going off over their heads, shooting, etc. So that there is experience and no unfamiliar new (and therefore frightening or, let’s say, spooky) feelings.
This is also the case in Web3, in my opinion. We need to spend more time on education. Maybe we should create some frameworks or applications where users or even projects or protocols can experience what it’s like to get scammed or hacked and “live” through it. It’s all about immersive and gamified learning.
But let’s get back to out primary topic…
Essentially. Nowadays, in my opinion, the ability to effectively inform clients of the specifics and status of an audit is seriously lacking in traditional auditing firms.
Logically, cybersecurity must be considered on every level of project development — with contests on the guard at the initial stage, followed by audits, and then bug bounties — at the final stage. No doubt, a new generation of cybersecurity products are already on the way that will cover all these aspects in one user-friendly interface.
Certain layers of the web3 security stack remain underutilized, which will most likely change as the industry matures. DeFi projects, in particular, may begin to broaden the scope of security activities to include proactive threat monitoring and response, as well as automated risk management (rather than focusing solely on vulnerability assessments).
Clients are often unaware of the precise steps taken during the audit or the process’s current status as a result of this lack of transparency. This lack of visibility consequently leads to a variety of problems. I want to add something important. There may be literally no better way to find bugs than to expose interfaces to the general public besides bug-bounty programs.
When attackers and defenders have access to the same information, it levels the playing field in a way that sharpens focus on prevention instead of response. That would allow our industry to address systemic weaknesses over time!
The Missing Piece
While bug bounty programs and audits are both essential for ensuring smart contract security, it is essential to recognize the critical importance of pre-auditing preparation. This often overlooked step can significantly impact the effectiveness and efficiency of the auditing process.
The combination of bug-bounty programs and audits offers a robust security mechanism for Web3 smart contracts. However, pre-auditing preparation plays a critical role in enhancing the overall security posture of a smart contract.
Thorough code review and comprehensive documentation of the smart contract’s functionality are fundamental pre-auditing preparations. Conducting internal code audits and ensuring clear and concise documentation allows auditors to understand the intended behavior of the contract accurately, accelerating the auditing process.
Integrating the smart contract with various platforms, protocols, or external systems can also expose potential vulnerabilities. Pre-auditing integration testing ensures that the smart contract functions seamlessly and securely within its intended ecosystem while minimizing risks associated with external dependencies.
By conducting thorough code reviews, integration testing, formal verification, and adopting secure development practices, developers can proactively address and mitigate potential risks before reaching the auditing phase. Consequently, developers and auditors collaborate more effectively, ensuring the creation of secure, resilient, and trustworthy Web3 smart contracts in the ever-evolving Web3 landscape.
Bonus Toolset: UX Core
A friend of mine, who, among many other cool things, created an absolute killer used by Product Managers at FAANG.
It’s a free tool to dive deep into cognitive science and human behavior, as well as a practical guide on how to use it. Check it out:
R.xyz Beta Launching Soon

Get ready for a seismic shift in cybersecurity. A revolution is on the horizon, set to redefine everything. Be a part of this groundbreaking change at #TrustX2023!
The Hexens.io team, which brings together more than 13 years of web2 and web3 experience, is well-positioned to address decentralized security issues. Through innovative tools and training, they hope to strengthen security procedures while encouraging innovation!
Here are just a few of the revolutionary things to be implemented in R.xyz:
-
Proof of duplicate;
-
Enormous emerge tools with no analogs existing;
-
Proper triage (triage by Hexens.io!)and white-hat advocate mechanism.
The project’s team also addresses the industry’s fundamental issues by encouraging transparency, raising standards, and providing guidance.
While details are not yet publicly disclosed, the vision seems impactful to me from insights shared so far. The team demonstrates a deep understanding of the most pressing pain points around security that developers and users face today. Their solutions could provide a welcome relief from those fronts — officercia.eth
This significant project adopts a broad perspective. The R’s team also hopes to build a thorough security ecosystem that will increase web3’s scalability and protection.
To let us know your interests and preferences better, please fill in a short questionnaire!
The team’s goal is to create a comprehensive security ecosystem that will improve web3’s scalability and protection overall. Following this project’s efforts to improve security standards across the developing web3 landscape will be fascinating, check it out and apply for a closed beta:
Following this project’s efforts to improve security standards across the developing web3 landscape will be fascinating. Their drive and knowledge inspire hope for advancement.
So that, I’d like to invite you to monitor their Twitter, Telegram & Discord for updates as the project develops. A stronger, safer web3 that lives up to its full potential will rely on efforts like this one!