In the fast-evolving world of blockchain and decentralized finance, smart contracts are the backbone of trustless systems. They automate transactions, manage assets, and enforce rules on immutable ledgers like Ethereum or Solana. However, this immutability cuts both ways: once deployed, a flawed smart contract can lead to catastrophic losses. According to reports, over $14.8 billion has been lost to crypto exploits between 2020 and 2024, with a 21% annual increase in incidents. Building a robust security pipeline isn’t just best practice — it’s essential for protecting user funds, protocol integrity, and your project’s reputation.
This article outlines a step-by-step guide to constructing a “bulletproof” smart contract security pipeline. We’ll cover everything from initial design to post-deployment monitoring, emphasizing layered defenses. Along the way, we’ll explore how tools like Guardrail.ai can supercharge your efforts, providing real-time protection that catches threats before they escalate.
Step 1: Understand the Risks and Lay the Foundation
Before writing a single line of code, map out the threat landscape. Common vulnerabilities include reentrancy attacks (e.g., the infamous DAO hack), integer overflows, access control flaws, and oracle manipulations. Tools like the Smart Contract Weakness Classification (SWC) registry from the Ethereum Foundation can help categorize these risks.
Key Actions:
-
Threat Modeling: Assemble a cross-functional team (developers, auditors, and security experts) to brainstorm attack vectors specific to your contract’s logic.
-
Secure Coding Standards: Adopt guidelines like those from ConsenSys’s Solidity best practices or OpenZeppelin’s secure libraries. Use formal languages like Vyper for added safety if Solidity feels too flexible.
-
Environment Setup: Integrate security from the start with tools like Slither (static analysis) in your CI/CD pipeline.
By front-loading risk assessment, you reduce the attack surface by up to 70%, according to industry benchmarks from firms like Trail of Bits.
Step 2: Implement Rigorous Development and Testing
Security isn’t a phase — it’s embedded in development. Treat testing as non-negotiable, aiming for 100% code coverage on critical paths.
Key Actions:
-
Unit and Integration Testing: Use frameworks like Foundry to write exhaustive tests. Simulate edge cases, such as gas limit exhaustion or flash loan manipulations.
-
Fuzz Testing: Employ tools like Echidna to bombard your contracts with random inputs, uncovering hidden bugs.
-
Formal Verification: For high-stakes contracts, use Certora to mathematically prove properties like “no unauthorized withdrawals.”
Automate this in your pipeline using GitHub Actions or CircleCI. A sample workflow: On every pull request, run static analysis, unit tests, and fuzzing — fail the build if coverage dips below 95%.
Step 3: Conduct Multi-Layered Audits
No contract is secure without external eyes. Audits validate your work but shouldn’t be a one-off event.
Key Actions:
-
Internal Reviews: Start with peer code reviews using platforms like Sherlockfor bug bounties within your team.
-
Third-Party Audits: Engage reputable firms like Quill Audits. Budget for at least two audits per major release.
-
Community Audits: Leverage platforms like Spearbit and Cantina for crowdsourced vulnerability hunting, often with rewards tied to severity.
Post-audit, address all findings with a remediation plan. Re-audit after fixes to close the loop.
Step 4: Deploy Securely with Runtime Protections
Deployment is where theory meets reality. Use multi-signature wallets for upgrades and timelocks for governance changes to prevent single points of failure.
Key Actions:
-
Staging Environments: Test on fork networks (e.g., Ganache or local forks) mirroring mainnet conditions.
-
Gas Optimization and Monitoring: Tools like Tenderly can simulate deployments and track gas usage.
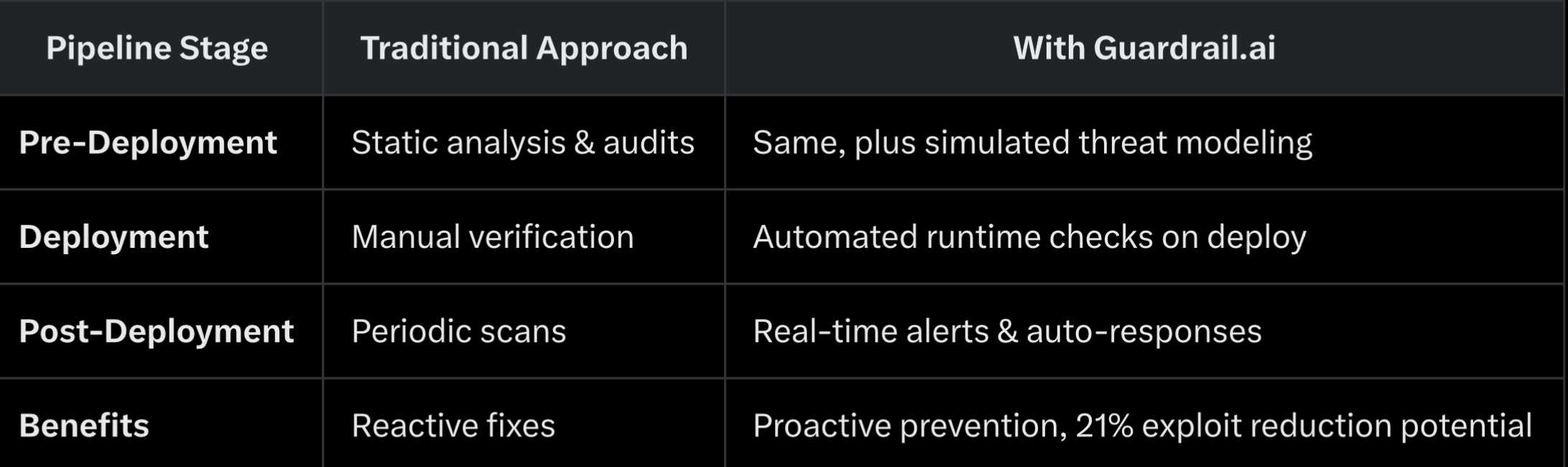
This is where runtime security shines. Post-deployment, your pipeline must evolve into continuous vigilance. Enter solutions like Guardrail.ai, a real-time DeFi security platform that monitors smart contracts across 24+ chains with sub-second scanning. Guardrail deploys over 295 customizable “guards” to detect anomalies, simulate risky transactions, and enforce runtime checks — preventing exploits before they drain funds. For instance, it can automatically pause vulnerable functions or flag malicious wallets, protecting over $1.3 billion in assets for leading protocols.
Integrating Guardrail into your pipeline is straightforward: Hook it into your DeFi stack via APIs for onchain monitoring of contracts, wallets, and bridges. It complements pre-deployment tools by providing full-stack defense, reducing reliance on fragmented monitoring solutions and slashing response times from hours to seconds.
Step 5: Foster Continuous Improvement and Incident Response
Security is iterative. Treat every incident as a learning opportunity.
Key Actions:
-
Incident Response Plan: Define playbooks for breaches, including off-chain coordination (e.g., via Discord alerts) and on-chain pauses.
-
Metrics and Feedback Loops: Track KPIs like mean time to detect (MTTD) vulnerabilities or false positive rates. Use dashboards from Dune Analytics for onchain metrics.
-
Regular Drills: Simulate attacks quarterly to test your pipeline’s resilience.
Tools like Guardrail enhance this by offering context-aware alerts that filter noise, ensuring your team focuses on real threats. Its automated responses — escalating to teams only when needed — streamline IR, turning potential disasters into minor hiccups.
Circuit Breakers: In-Depth
Most developers think circuit breakers are just smart contract functions — a pause() button activated when thresholds are breached. But that’s only half the story.
Circuit breakers in smart contracts aren’t just code features — they’re monitoring systems that detect anomalies and trigger protective responses in real-time. While ERC-7265 standardizes onchain circuit breakers, the real innovation lies in intelligent monitoring that acts as an external circuit breaker, catching attacks within seconds and preventing billions in losses before they happen.
The Evolution: Static code protections → Real-time behavioral monitoring → Predictive threat prevention
How Monitoring Could Have Prevented Recent Major Exploits
1 — The Resupply attack ($9.6M) — June 2025
What happened: Donation attack exploited empty vault to manipulate exchange rates.
Traditional circuit breaker: Would only trigger after withdrawals exceeded thresholds.
Monitoring circuit breaker would have caught:
-
Unusual donation patterns to new vaults
-
Extreme share price inflation in real-time
-
Minimal collateral backing massive loans
Result: Attack stopped in 2 minutes vs. 90 minutes of actual drainage
2 — The Arcadia finance exploit ($3.5M) — July 2025
What happened: Circuit breaker gaming + malicious router injection.
Traditional circuit breaker: Was actively disabled by attacker’s strategy.
Monitoring circuit breaker would have detected:
-
Suspicious contract deployment patterns (bait attack)
-
Non-DEX router addresses in swap operations
-
Coordinated multi-day attack preparation
Result: $3.4M saved through early pattern detection
3 — The BigONE exchange hack ($27M) — July 2025
What happened: Supply chain attack compromised hot wallet logic.
Traditional circuit breaker: Couldn’t detect compromised third-party software.
Monitoring circuit breaker would have identified:
-
Abnormal hot wallet withdrawal patterns
-
Unusual cross-chain coordination
-
Behavioral deviations in operational systems
Result: Losses limited to under $1M through rapid anomaly detection!
The Technical Architecture of Monitoring Circuit Breakers
Level 1: Monitoring alerts (0–30 seconds)
-
Detect unusual patterns
-
Generate risk scores
-
Alert security teams
Level 2: Automated response (30–60 seconds)
-
Rate limiting suspicious addresses
-
Temporary transaction delays
-
Protocol notifications
Level 3: Emergency activation (60–120 seconds)
-
Trigger onchain circuit breakers
-
Coordinate cross-protocol response
-
Implement emergency pauses
Modern monitoring circuit breakers incorporate:
-
Historical attack data for pattern matching
-
Cross-protocol threat intelligence
-
Real-time vulnerability assessments
-
Predictive modeling for emerging threats
Regulators increasingly view monitoring circuit breakers as:
-
Due diligence requirements for DeFi protocols
-
Risk management standards for institutional participation
-
Consumer protection measures for retail users
-
Systemic risk mitigation for the broader financial system
Circuit breakers aren’t just code — they’re systems:
-
Onchain mechanisms provide last-line defense
-
Real-time monitoring enables proactive protection
-
Predictive analytics prevent attacks before they start
-
Coordinated response protects entire ecosystems
Important takeaway to note:
-
Deploy monitoring before you need it — attacks happen without warning
-
Integrate multiple monitoring sources for comprehensive coverage
-
Plan graduated responses to balance security and usability
-
Prepare for false positives with override mechanisms
Conclusion
Building a bulletproof smart contract security pipeline demands discipline, but the payoff is immense: resilient protocols that scale with confidence. Start small — integrate one new tool per sprint — and scale up. By layering design, testing, audits, deployment safeguards, and monitoring, you’ll outpace adversaries.
For that final layer of defense, implementing Guardrail.ai isn’t just helpful — it’s transformative. It shifts your pipeline from static to dynamic, guarding against the unpredictable nature of live blockchains. As DeFi matures, protocols that prioritize such real-time security won’t just survive; they’ll thrive. Ready to lock it down? Audit your contracts today and explore Guardrail at guardrail.ai